Introduction
The concept of the access control system in the contemporary world is found in daily lives. It is there while entering into a building or logging into an online bank account or social media account. The access control system has put the environment under control as individual security is a priority and primary concern here. Along with this, different smart card technologies are on the go for tight security applications and for delivering more proper access control. Smart card technology refers to the plastic card containing an embedded computer chip advocating microprocessor chip or memory (CAI, 2008). This report aims to concentrate on the aspects of the access control environment and discuss the application of smart cards technology in light of such access control scenarios.
Source: (Kim & Park, 2021).
On the other hand, this report would focus on highlighting the significance of smart cards in the access control environment, explaining their applicability and benefits at the same time. The convenience and demand of security for any transaction has increased the deployment of smart cards with higher relevance. Nonetheless, the report describes different technologies involved in smart card applications and their future trends to analyse the path for technology usage. It also shows how the smart card technology has enriched the access control environment and its ability to adhere to the security requirement contemporarily (Atmojo et al. 2011). Hence, the aspects related to the smart card technology would be manifesting a clear idea about the topic and its relevance in the same context.
Structure and Functionalities of Smart Cards Technology
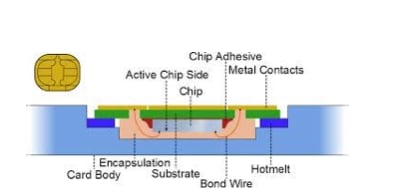
The structure or the relevance of smart card has made the concept highly demandable and adapted in the contemporary world of digital dominance. The structure of a smart card is developed with plastic and metal chips intact, and the smart card is manufactured out of silicon wafers that are attached to aluminium contact areas (Faroqi & Mesbah, 2021). The smart card quoted with epoxy resin embedded in plastic card that increases the efficiency of its functioning during any usage. On the other hand, the smart card operates through the power supplied by an electrical connector incorporated inside the card reader. This can create a radio frequency transmission for the contactless reading of frequencies of different channels (Gupta & Quamara, 2018). An identity based access control and mutual authentication framework are used for distributed cloud computing services in IoT environment . There are four main components of a smart card: central Processing Unit, read-only memory, Random Access Memory, and application memory.
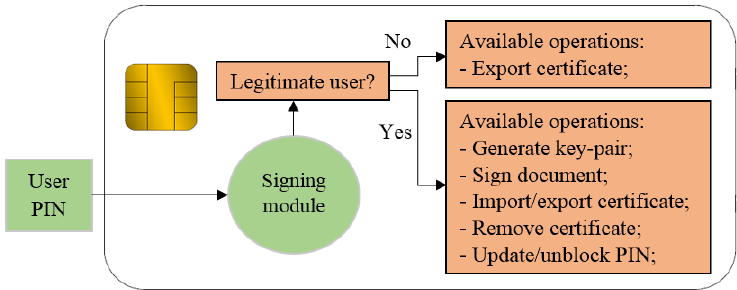
The function of a smart card is identified to provide security identified and authenticated information transformation to the holder and the third party sources. The smart card would also provide and gain access to the information using pin code or biometric data that are commonly used for authen ication (Gupta & Qu mara, 2018). Apart from this, with the help of smart cards, a secure way of data storing and protected communication can be conducted with encryption.
Technologies Of Smart Cards in Access Control Environment
To discuss the technologies included in the smart cards in an access control environment, it is observed that since the inception of contactless smart card is delivered on ISO/IEC 7810 card bodies. Other features or functionalities are automatically be associated with the plastic card that can be utilised in a juncture with the contactless technology (Haratiannejadir & Selmic, 2020). The Technologies include;
- Magnetic stripes
- Holograms
- Contact chips
- Barcodes
- Corporate logos
- Photo personalization via dye sublimation printing
- Image customisation via dye sublimation printing
- Punch slot for lanyards
- Signature panels (Khan et al. 2016).
Along with these features, the technologies of the smart card involve different aspects while the technology and its main purpose is used to secure data storage that a smart card system could carry efficiently (Khan et al. 2016). The smart card technology is one of the main storage card technology that smart cards generally involves. The optical character recognition technology helps in the development of two types of cards for storing machine or human-readable data such as the embossed card and the optical stripe card.
Embossed card has the most basic feature that are aligned with the credit cards and it enables the computer to read the financial data or individual data using contactless scanning. Most importantly, the pattern hidden in the card can be detected by specialised reader included within the chip format.
In case of optical bar code cards, it is enabled for both machine usage and human intervened use. The bar code card is being developed using series of thin and thick parallel lines incorporated and embedded within the plastic surface with microchip patterns. Apart from this, another technology is detected in the due course of smart card is machine readable technology (Khot, 2016). Though there are smart cards that are developed with technologies readable both by humans and machines, but currently there are technologies that are readable by machines only.
In most cases and in the wake of contemporary digital vulnerabilities, the machine readability is demanded at its peak. Therefore, except for these two types of technologies, the contemporary access control environment is demanding contactless smart card technology. This advocates the minimum contact with machines as the machine readability are also showing chances of data contamination. Hence, based on the technology identification, it can be identified that multiple technologies over a single credential are effective in providing excellent solutions for many circumstances (Kim & Park, 2021).
One instance of the effectiveness and efficiency is the combination of high performance that keeps the processor contact card on priority. It helps in securing the network and another contactless technology is evident in generating physical access control over a single photo ready identity credential. Another significant use of the smart card technology is to facilitate the migration between one access control technology to another for an extended period of time. While the entire function is being carried out based on a piece of cardholder information (Haratiannejadir & Selmic, 2020).
If the smart card technology is analysed, the contactless smart card technology is dominating the physical access control environment. One of the significant technologies as an example for a contactless secure smart card technology is iCLASS technology from each HID used for physical access control environment. This particular technology is ISO/IEC 15693 compliant and operates at 13.56 MHz. It also offers high-speed communication features and carries special features for digital cash applications and encryption protocol. Apart from this, two memory sizes are available with the iCLASS contactless card that contains 2k bit and 16 kbit (Lu et al. 2015). The 2Kbit is basically used for physical access control data which enables the smart cards to carry a memory that can be divided into 2 or 16 separate areas. Applications that need technologies like fingerprint biometrics and authentication are unable to use more than one segment when required. But it makes the usage of the smart card very efficient with the available memory.
Therefore, certain features of smart cards technologies are highlighted to understand the way it dominates and successful in addressing all the requirements of the contemporary physical access control environment (Khot, 2016). The ultraviolet fluorescent is invisible to the naked eye but is used to authenticate the card when placed under ultraviolet light. Holograms are accepted as security measures for such technology that the contemporary smart cards are adapting. It secures the physical access control environment with the recognisable security measures and identification of counterfeit cards (Nedjah, et al. 2017). Hence, contactless smart card technologies are well equipped and suited for the access control environment contemporarily. It is also evident in providing a higher level of security than the traditional access control technologies and their platforms.
Benefits of smart card in access control environment
The contemporary access control environment has become fragile due to continuous technological advancement and digital violations. For that reason, smart card technologies are continuously changing on the go. In this segment of the reports, the benefits of smart card technology in the access control environment are discussed to highlight its positive impact in critical manner (Khot, 2016). With the smart card technologies, the building access system and their security controllers have become more accurate. The different actors of a building security system have different types of card access control system which increases the authenticated security measures.
As the smart cards enable containing personal information through a computer chip program, hence, the cardholder’s is able to access any point of a digital application from any device using the smart card (Kim & Park, 2021). Most importantly, the beneficial aspect of the smart card is that it has integrated different technology-enabled program that includes property proximity magnetic stripes and a biometric system. Such systems allow the cardholder to access different information from different locations with secure channels.
Apart from this, with smart card technology the access control system can be securely operated. In terms of transaction and banking facilities the smart card technology has played a significant role in managing personal information and financial data without getting violated (Haratiannejadir & Selmic, 2020). These are the benefits of smart card technologies in the current wake of access control environment. While the future facilities are subjected to be evaluated to understand its benefits as well.
Challenges of smart card technology in Access Control Environment
Along with the advantages of smart card in the access control environment, there are certain challenges important to create a balance between its positive and negative impact. Therefore, the challenges are;
- Though smart cards are identified as the most secure channel for any information or transaction but in the actual smart cards can give compromised security.
- Despite the standard security protocols incorporated in Visa and MasterCard the smart cards are still not violated (Nedjah, et al. 2017).
- Most of the companies like Mondex have created smart card that can only transact between Mondex cards but this has also created challenges for smart card technologies to reach their full potential.
- Another issue in this regard is identified with the security that involves the public perception of the technology.
- As the public and the community members start to understand that the smart card is not secure enough there could be a negative impact on the usage of smart card due to the lack of proper information or knowledge.
- The most significant issue or challenge that smart cards nowaday are facing is the pricing of the card readers or its internal materials that cause companies to look for alternatives (Haratiannejadir & Selmic, 2020).
- Despite of the challenges, the smart card technologies are daunting and dominating its region of expertise and the future trends are effective enough to manifest its viability in the due course.
Future Trends of Smart Cards Technology
In the context of analysing the future trends of smart card, it is important to understand the future directions or future trends related to the applicability and functionalities of markets in access control systems. Therefore, the future trends for the smart cards can be discussed in a comparative manner while highlighting today’s trends as well (Khan et al. 2016). Firstly, firstly the contemporary smart cards have 8 to 32 KB of memory which is likely to increase in the future courses of smart card applicable in the parallel development of Information and communication technology.
The computational power of the smart cards would also be subject to increase as the computational power of the smart cards would also be subjected to increase as the contemporary computational powers are limited. Controlling the problem of overheating has always been a significant challenge for smart card technology but in future, the problem can get bigger if a proper measure is not implemented. The computational power of future smart cards with increase with additional encryption and statistical data development (Kim & Park, 2021). The future trends of a smart card also involves the application of real-time encryption of speech or video identity which Are not available or applicable in the current market trend of smart card technology.
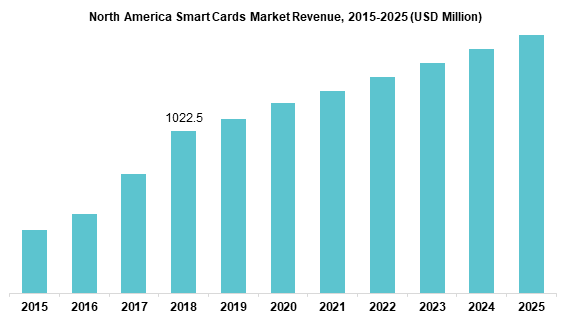
As the investments are increasing the development and supplier of cryptographic hardware within the smart card is adapted and considered for the future course of operations and are subjected to dominate the future market of the access control environment. The market size of the smart card technology is likely to grow by 2025 with 16% in comparison to the current status (Haratiannejadir & Selmic, 2020). The Java API and well-designed card independent programming environment is still at its infancy stage and it is assumed that the future trend would adopt the Java API system within the smart card Technology. The development of Java language is also considered for the future course of action while many companies are considering Java language incorporated within their smart card technology and access control system. Another significant change that the smart card technology would encounter in future is the replacement of the smart card with the I button device which is designed for hard circumstances. It is able to carry a much longer lifetime than the smart card (Khan et al. 2016). Most significantly, smart card holders currently are relied on the plastic form of smart cards. But in future, the owners or cardholders would be able to connect the smart card with their smart phones which will increase the security measures a lot.
Conclusion
In conclusion, it can be stated that the report has focused on the current trends in the biometrics area and intended to discuss smart card technology in the access control environment. The aim of this report is to manifest standard information and the idea of smart card technology in the current digitalised world and how it has been effective in providing security so far. The report has provided a detailed discussion over the structure and function of the smart card while it has also been evaluated the technologies involved in smart card and their application in the access control system. Along with this, the benefits of the smart card and its challenges are discussed so that a balanced form of an idea can be generated. Most importantly, the future trends of the smart cards are discussed in the light of a comparison where the trends that today’s market are following with smart cards have also been highlighted. In this regard, a comparative understanding of what the current smart cards are providing to its customers or the world and what future would be able to provide can better be presented.
References
Atmojo, U., Litasari, & Irfansyah, A. (2011). Single Board Computer Based Building Security Management System: Contactless Smart Card for Automatic Door Access Control System. Applied Mechanics And Materials, 110-116, 4816-4822. https://doi.org/10.4028/www.scientific.net/amm.110-116.4816
CAI, J. (2008). New dynamic password authentication based on smart card and fingerprint. Journal Of Computer Applications, 28(5), 1167-1169. https://doi.org/10.3724/sp.j.1087.2008.01167
Faroqi, H., & Mesbah, M. (2021). Inferring trip purpose by clustering sequences of smart card records. Transportation Research Part C: Emerging Technologies, 127, 103131. https://doi.org/10.1016/j.trc.2021.103131
Gupta, B., & Quamara, M. (2018). An identity based access control and mutual authentication framework for distributed cloud computing services in IoT environment
using smart cards. Procedia Computer Science, 132, 189-197. https://doi.org/10.1016/j.procs.2018.05.185
Haratiannejadi, K., & Selmic, R. (2020). Smart Glove and Hand Gesture-Based Control Interface for Multi-Rotor Aerial Vehicles in a Multi-Subject Environment. IEEE Access, 8, 227667-227677. https://doi.org/10.1109/access.2020.3045858
Khan, M., Silva, B., & Han, K. (2016). Internet of Things Based Energy Aware Smart Home Control System. IEEE Access, 4, 7556-7566. https://doi.org/10.1109/access.2016.2621752
Khot, S. (2016). A Survey on Smart Ration card system using RFID and Biometrics. International Journal Of Engineering And Computer Science. https://doi.org/10.18535/ijecs/v5i12.45
Kim, J., & Park, N. (2021). Role‐based Access Control Video Surveillance Mechanism Modeling in Smart Contract Environment. Transactions On Emerging Telecommunications Technologies. https://doi.org/10.1002/ett.4227
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). A biometrics and smart cards-based authentication scheme for multi-server environments. Security And Communication Networks, 8(17), 3219-3228. https://doi.org/10.1002/sec.1246
Nedjah, N., Wyant, R., Mourelle, L., & Gupta, B. (2017). Efficient yet robust biometric iris matching on smart cards for data high security and privacy. Future Generation Computer Systems, 76, 18-32. https://doi.org/10.1016/j.future.2017.05.008
1 thought on “Smart Card Technology Thriving into the Access Control Environment”